
Choose Ukrainian authorities networks have remained contaminated with a malware referred to as OfflRouter since 2015.
Cisco Talos mentioned its findings are primarily based on an evaluation of over 100 confidential paperwork that have been contaminated with the VBA macro virus and uploaded to the VirusTotal malware scanning platform.
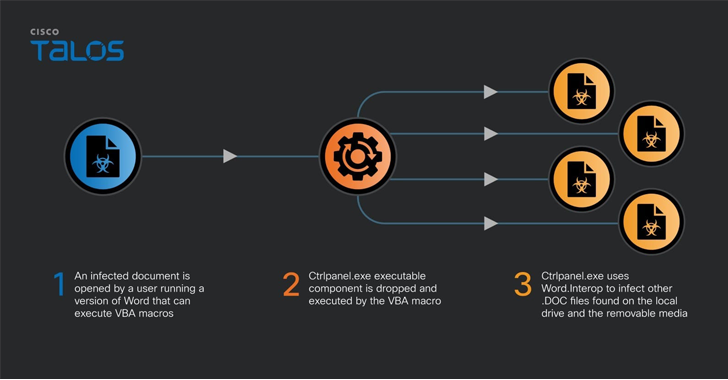
“The paperwork contained VBA code to drop and run an executable with the title ‘ctrlpanel.exe,'” safety researcher Vanja Svajcer mentioned. “The virus remains to be lively in Ukraine and is inflicting probably confidential paperwork to be uploaded to publicly accessible doc repositories.”
A placing side of OfflRouter is its lack of ability to unfold by way of e mail, necessitating that or not it’s propagated by way of different means, resembling sharing paperwork and detachable media, together with USB reminiscence sticks containing the contaminated paperwork.
These design selections, intentional or in any other case, are mentioned to have confined the unfold of OfflRouter inside Ukraine’s borders and to some organizations, thus escaping detection for nearly 10 years.

It is presently not identified who’s answerable for the malware and there aren’t any indications that it was developed by somebody from Ukraine.
Whoever it’s, they’ve been described as creative but inexperienced owing to the weird propagation mechanism and the presence of a number of errors within the supply code.
OfflRouter has been beforehand highlighted by MalwareHunterTeam as early as Might 2018 and once more by the Pc Safety Incident Response Group Slovakia (CSIRT.SK) in August 2021, detailing contaminated paperwork uploaded to the Nationwide Police of Ukraine’s web site.
The modus operandi has remained just about unchanged, with the VBA macro-embedded Microsoft Phrase paperwork dropping a .NET executable named “ctrlpanel.exe,” which then infects all recordsdata with the .DOC (not .DOCX) extension discovered on the system and different detachable media with the identical macro.
“The an infection iterates by means of a listing of the doc candidates to contaminate and makes use of an revolutionary methodology to test the doc an infection marker to keep away from a number of an infection processes – the perform checks the doc creation metadata, provides the creation occasions, and checks the worth of the sum,” Svajcer mentioned.
“If the sum is zero, the doc is taken into account already contaminated.”
That mentioned, the assault turns into profitable solely when VBA macros are enabled. Microsoft, as of July 2022, has been blocking macros by default in Workplace paperwork downloaded from the web, prompting risk actors to hunt different preliminary entry pathways.
One other key perform of the malware is to make Home windows Registry modifications in order to make sure that the executable runs each time upon booting the system.
“The virus targets solely paperwork with the filename extension .DOC, the default extension for the OLE2 paperwork, and it’ll not attempt to infect different filename extensions,” Svajcer elaborated. “The default Phrase doc filename extension for the more moderen Phrase variations is .DOCX, so few paperwork shall be contaminated because of this.”

That is not all. Ctrlpanel.exe can also be outfitted to seek for potential plugins (with the extension .ORP) current on detachable drives and execute them on the machine, which suggests the malware is anticipating the plugins to be delivered by way of USB drives or CD-ROMs.
One the opposite, if the plugins are already current on a bunch, OfflRouter takes care of encoding them, copying the recordsdata to the basis folder of the hooked up detachable media with the filename extension .ORP, and manipulating them to make them hidden in order that they don’t seem to be seen by means of the File Explorer when plugging them into one other gadget.
That mentioned, one main unknown is whether or not the preliminary vector is a doc or the executable module ctrlpanel.exe.
“The benefit of the two-module virus is that it may be unfold as a standalone executable or as an contaminated doc,” Svajcer mentioned.
“It could even be advantageous to initially unfold as an executable because the module can run standalone and set the registry keys to permit execution of the VBA code and altering of the default saved file codecs to .DOC earlier than infecting paperwork. That method, the an infection could also be a bit stealthier.”

