
The malicious code inserted into the open-source library XZ Utils, a extensively used package deal current in main Linux distributions, can also be able to facilitating distant code execution, a brand new evaluation has revealed.
The audacious provide chain compromise, tracked as CVE-2024-3094 (CVSS rating: 10.0), got here to mild final week when Microsoft engineer and PostgreSQL developer Andres Freund alerted to the presence of a backdoor within the information compression utility that provides distant attackers a technique to sidestep safe shell authentication and acquire full entry to an affected system.
XZ Utils is a command-line software for compressing and decompressing information in Linux and different Unix-like working techniques.
The malicious code is claimed to have been intentionally launched by one of many challenge maintainers named Jia Tan (aka Jia Cheong Tan or JiaT75) in what seems to be a meticulous assault spanning a number of years. The GitHub consumer account was created in 2021. The identification of the actor(s) is presently unknown.

“The menace actor began contributing to the XZ challenge virtually two years in the past, slowly constructing credibility till they got maintainer obligations,” Akamai stated in a report.
In an additional act of intelligent social engineering, sockpuppet accounts like Jigar Kumar and Dennis Ens are believed to have been used to ship function requests and report quite a lot of points within the software program with the intention to drive the unique maintainer – Lasse Collin of the Tukaani Undertaking – so as to add a brand new co-maintainer to the repository.
Enter Jia Tan, who launched a collection of modifications to XZ Utils in 2023, which ultimately made their technique to launch model 5.6.0 in February 2024. Additionally they harbored a classy backdoor.
“As I’ve hinted in earlier emails, Jia Tan could have a much bigger function within the challenge sooner or later,” Collin stated in an alternate with Kumar in June 2022.
“He has been serving to loads off-list and is virtually a co-maintainer already. 🙂 I do know that not a lot has occurred within the git repository but however issues occur in small steps. In any case some change in maintainership is already in progress at the very least for XZ Utils.”
The backdoor impacts XZ Utils 5.6.0 and 5.6.1 launch tarballs, the latter of which incorporates an improved model of the identical implant. Collins has since acknowledged the challenge’s breach, stating each the tarballs have been created and signed by Jia Tan and that that they had entry solely to the now-disabled GitHub repository.
“That is clearly a really complicated state-sponsored operation with spectacular sophistication and multi-year planning,” firmware safety firm Binarly stated. “Such a posh and professionally designed complete implantation framework is just not developed for a one-shot operation.”
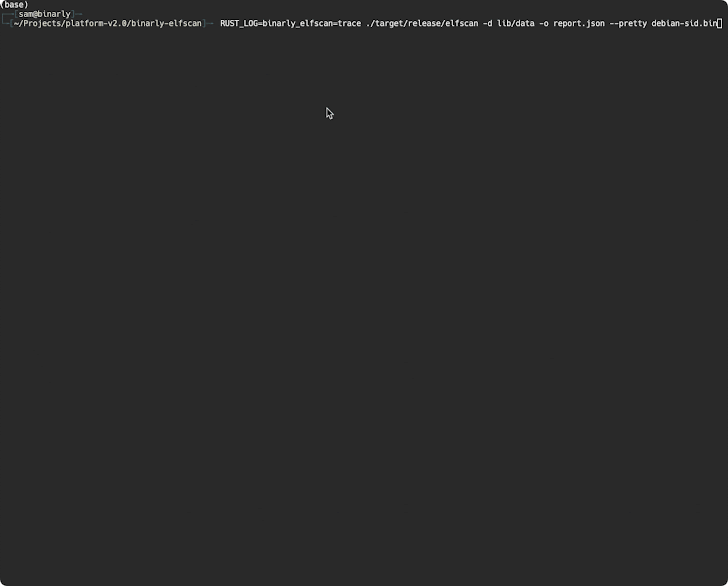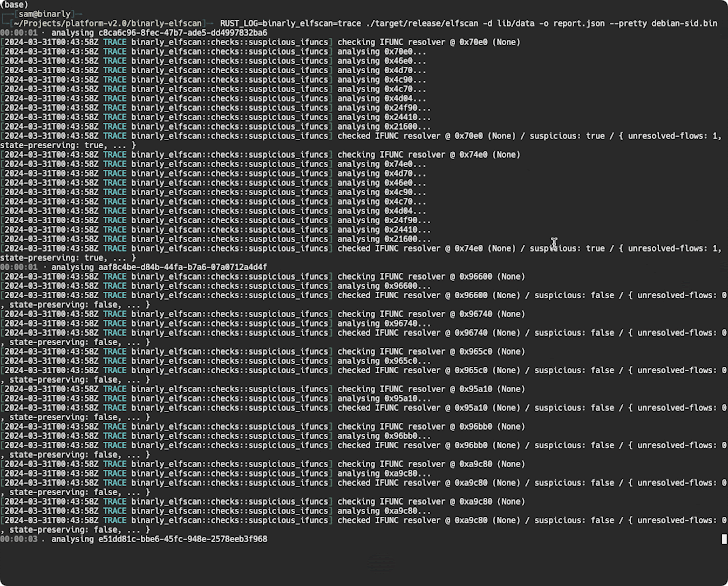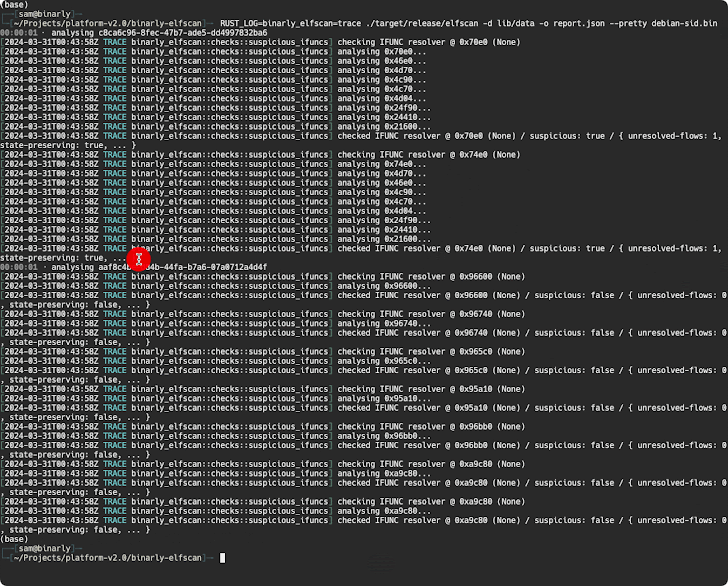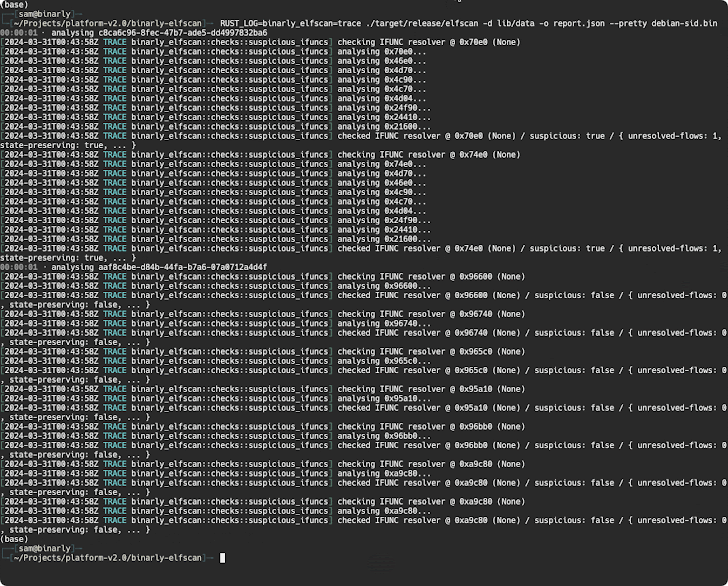
A deeper examination of the backdoor by open-source cryptographer Filippo Valsorda has additionally revealed that the affected variations enable particular distant attackers to ship arbitrary payloads via an SSH certificates which will probably be executed in a fashion that circumvents authentication protocols, successfully seizing management over the sufferer machine.
“It seems as if the backdoor is added to the SSH daemon on the weak machine, enabling a distant attacker to execute arbitrary code,” Akamai stated. “Which means any machine with the weak package deal that exposes SSH to the web is probably weak.”

In different phrases, the backdoor permits a distant attacker with a predetermined non-public key to hijack the SSH daemon with the intention to execute malicious instructions.
For sure, the unintentional discovery by Freund is likely one of the most important provide chain assaults found to this point and will have been a extreme safety catastrophe had the package deal been built-in into steady releases of Linux distributions.
“Probably the most notable a part of this provide chain assault is the intense ranges of dedication of the attacker, working greater than two years to determine themselves as a respectable maintainer, providing to choose up work in varied OSS initiatives and committing code throughout a number of initiatives with the intention to keep away from detection,” JFrog stated.
As with the case of Apache Log4j, the incident as soon as once more highlights the reliance on open-source software program and volunteer-run initiatives, and the implications that might entail ought to they endure a compromise or have a serious vulnerability.
“The larger ‘repair’ is for organizations to undertake instruments and processes that enable them to determine indicators of tampering and malicious options inside each open supply and industrial code utilized in their very own growth pipeline,” ReversingLabs stated.

