
The maintainers of the Python Bundle Index (PyPI) repository briefly suspended new person sign-ups following an inflow of malicious initiatives uploaded as a part of a typosquatting marketing campaign.
PyPI mentioned “new challenge creation and new person registration” was quickly halted to mitigate what it mentioned was a “malware add marketing campaign.” The incident was resolved 10 hours later, on March 28, 2024, at 12:56 p.m. UTC.
Software program provide chain safety agency Checkmarx mentioned the unidentified risk actors behind flooding the repository focused builders with typosquatted variations of standard packages.
“It is a multi-stage assault and the malicious payload aimed to steal crypto wallets, delicate information from browsers (cookies, extensions information, and many others.), and numerous credentials,” researchers Yehuda Gelb, Jossef Harush Kadouri, and Tzachi Zornstain mentioned. “As well as, the malicious payload employed a persistence mechanism to outlive reboots.”
The findings have been additionally corroborated independently by Mend.io, which famous that it detected greater than 100 malicious packages concentrating on machine studying (ML) libraries comparable to Pytorch, Matplotlib, and Selenium.

The event comes as open-source repositories are more and more turning into an assault vector for risk actors to infiltrate enterprise environments.
Typosquatting is a well-documented assault approach by which adversaries add packages with names intently resembling their reliable counterparts (e.g., Matplotlib vs. Matplotlig or tensorflow vs. tensourflow) as a way to trick unsuspecting customers into downloading them.
These misleading variants – totalling over 500 packages, per Test Level – have been discovered to be uploaded from a novel account beginning March 26, 2024, suggesting that the entire course of was automated.
“The decentralized nature of the uploads, with every package deal attributed to a special person, complicates efforts to cross-identify these malicious entries,” the Israeli cybersecurity firm mentioned.
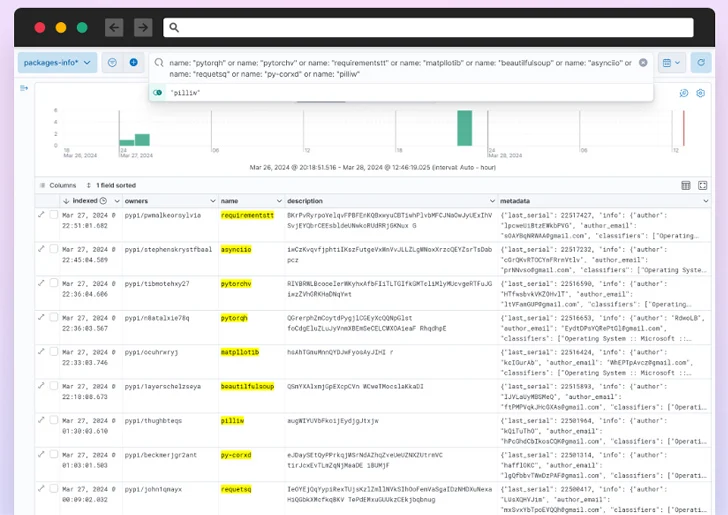
Cybersecurity agency Phylum, which has additionally been monitoring the identical marketing campaign, mentioned the attackers printed –
- 67 variations of necessities
- 38 variations of Matplotlib
- 36 variations of requests
- 35 variations of colorama
- 29 variations of tensorflow
- 28 variations of selenium
- 26 variations of BeautifulSoup
- 26 variations of PyTorch
- 20 variations of pillow, and
- 15 variations of asyncio
The packages, for his or her half, examine if the installer’s working system was Home windows, and in that case, proceed to obtain and execute an obfuscated payload retrieved from an actor-controlled area (“funcaptcha[.]ru”).

The malware capabilities as a stealer, exfiltrating recordsdata, Discord tokens, in addition to information from net browsers and cryptocurrency wallets to the identical server. It additional makes an attempt to obtain a Python script (“hvnc.py”) to the Home windows Startup folder for persistence.
The event as soon as once more illustrates the escalating danger posed by software program provide chain assaults, making it essential that builders scrutinize each third-party part to make sure that it safeguards towards potential threats.
This isn’t the primary time PyPI has resorted to such a measure. In Could 2023, it quickly disabled person sign-ups after discovering that the “quantity of malicious customers and malicious initiatives being created on the index previously week has outpaced our potential to answer it in a well timed style.”
PyPI suspended new person registrations a second time on November 24, 2023, which it resolved 10 days later, and once more on December 27 for comparable causes. It was subsequently lifted on January 2, 2024.

